Isakmp
IKE establishs the shared security policy and authenticated keys. IKE or Internet Key Exchange protocol is a protocol that sets up Security Associations SAs in the IPSec protocol suite.

Isakmp Sa Negotiation In Aggressive Mode Download Scientific Diagram
The new config is based on a template that weve used at nearly 200 stores with no problems at all.

Isakmp. ISAKMP is distinct from key exchange protocols in order to cleanly separate the details of security association management and key management from the details of key exchange. The encryption command specifies which encryption. Numbers can range between 110000.
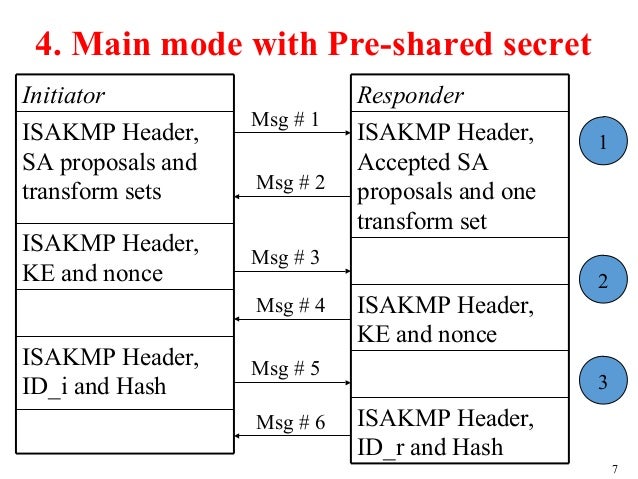
Main mode consists of three exchanges to process and validate the diffie-hellman exchange while aggressive mode does so within a single. It is also commonly called Internet Key Exchange IKE This page is very much a stub. The isakmp nat keepalive 5-3600 command is used when the router supports IPsec client connections.
The ISAKMP protocol state machine is defined so deleted messages will not cause a partial SA to be created the state machine will clear all state and return to idle. For more details about the ISAKMP header see RFC2408. Typically ISAKMP uses UDP as.
ISAKMP defines header and payload formats but needs an instantiation to a specific set of. And ISAKMP or Internet Security Association and Key Management Protocol is a protocol that is used to establish SA and cryptographic keys. The remote peer checks all of the peers policies against each of its configured policies in priority order highest priority first until it discovers a match.
There may be many different key exchange protocols each with different security properties. Typically ISAKMP uses UDP as its. Please help expand it.
Up to 5 cash back In ISAKMP SA and key management are separate from any key exchange protocols. Please help expand it. ISAKMP defines procedures and packet formats to establish negotiate modify and delete Security Associations.
ISAKMP is the protocol that specifies the mechanics of the key exchange. Port 500 is used by the Internet key exchange IKE that occurs during the establishment of secure VPN tunnels. When ISAKMP negotiations begin the peer that initiates the negotiation sends all of its policies to the remote peer and the remote peer tries to find a matc h.
ISAKMP is part of IKE. The 831 is running IOS v124 25d. Apr 28 115444 1146205484 pluto18126.
ISAKMP SA established means phase 1 connection is successfully established. The confusion for me is that in the Cisco IOS ISAKMPIKE are used to refer to the same thing. In the absence of traffic from the client a keepalive packet is sent if traffic is.
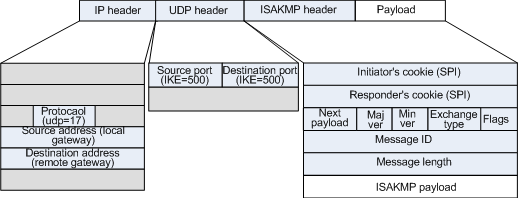
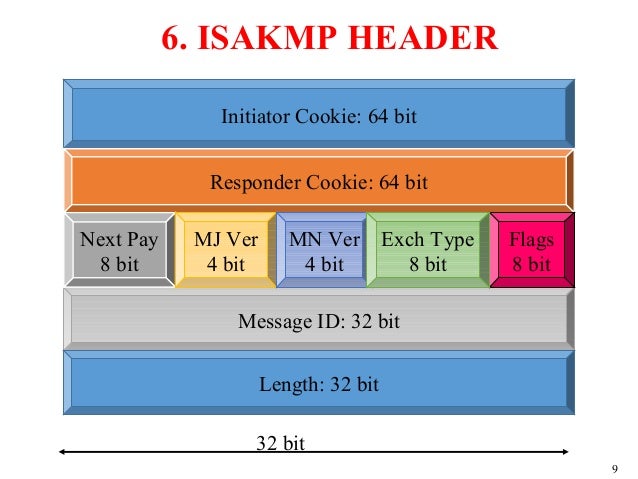
IPsec Overview TheASAusesIPsecforLAN-to-LANVPNconnectionsandprovidestheoptionofusingIPsecfor client-to-LANVPNconnectionsInIPsecterminologyapeer isaremote. Internet Security Association and Key Management Protocol ISAKMP The ISAKMP protocol is defined in RFC 2408. The following diagram shows the subfields that are contained in the ISAKMP_Header.
Please note that in a successful exchange the logs should display ISAKMP-SA established and some information specific to that association. Main mode and aggressive mode. History XXX - add a brief description of ISAKMP history Protocol dependencies UDP.
During this error the client machine keeps sending ISAKMP negotiation requests to the firewall but the client not getting any response from the firewall. What does ISAKMP abbreviation stand for. ISAKMP features prevent these types of attacks from being successful.
ISAKMP is a key exchange architecture or framework used within IPsec which manages the exchange of keys between both endpoints. Executing this command takes you to a subcommand mode where you enter the configuration for the policy. Contains the information that is required by the protocol to maintain state process payloads and possibly prevent denial-of-service or replay attacksThis is the standard ISAKMP header.
I did not send a certificate because I do not have one. IKE has ISAKMP SKEME and OAKLEY. IKE has ISAKMP SKEME and OAKLEY.
- Management of keys-Authentication - To authenticate peer gateway devices. However a common framework is required for agreeing to the format of SA. List of 10 best ISAKMP meaning forms based on popularity.
Internet Security Association and Key Management Protocol ISAKMP Description. ISAKMP_Header 28 bytes. XXX - add a brief description of ISAKMP history.
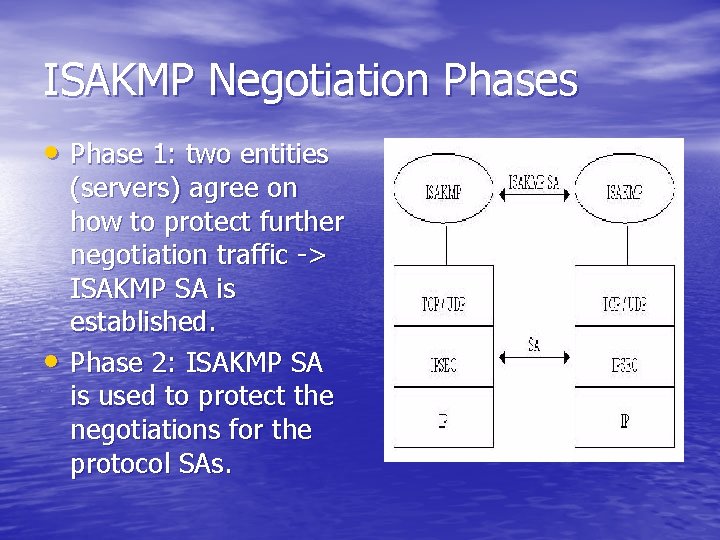
Log will also display the parameters defined for the phase 1. IKE establishes the security association SA between two endpoints through a three-phase process. It is also commonly called Internet Key Exchange IKE This page is very much a stub.
While connecting to the Global VPN Client a log entry The peer is not responding to phase 1 ISAKMP requests will be generated. Users of VPN servers and clients may encounter this port. Internet Security Association and Key Management Protocol ISAKMP The ISAKMP protocol is defined in RFC 2408.
SAs contain all the information required for execution of various network security services such as the IP layer services such as header authentication and payload encapsulation transport or application layer services or self-protection of negotiation traffic. Most common ISAKMP abbreviation full forms updated in August 2021. The crypto isakmp policy command creates a unique ISAKMPIKE management connection policy on the router where each policy requires a separate number.
IKE is a type of ISAKMP Internet Security Association Key Management Protocol implementation which is a framework for authentication and key exchange. So in a sense ISAKMP is an abstract protocol it provides a framework for authentication and key management and supports many actual key exchange protocols eg IKE. Some of the key requirements achieved using ISAKMP are detailed below.
IKE establishs the shared security policy and authenticated keys. ISAKMP is the protocol that specifies the mechanics of the key exchange. The confusion for me is that in the Cisco IOS ISAKMPIKE are used to.
The linking of the ISAKMP exchanges prevents the insertion of messages in the protocol exchange. This is one of the failure messages. However when we try changing the remote configuration with a replacement startup-config the VPN tunnel never comes up and in fact it seems to be failing in isakmp phase 1.
ISAKMP is part of IKE. Phase 1 has two possible modes.

The Difference Between Ike And Isakmp Protocol The Security Buddy

Isakmp Ikev1 Protocol Overview Wireshark Analysis Youtube
Isakmp Presented By Gary Aoki Linan Chang Thu

Deploying An Ipsec Secure Channel Isakmp Sa Empty Network Engineering Stack Exchange

Isakmp Sa Negotiation In Aggressive Mode Download Scientific Diagram

Internet Security Association And Key Management Protocol Isakmp The Ims Ip Multimedia Concepts And Services Second Edition Book

Gdoi Phase 1 Authentication Based On Isakmp Exchanges The Indicates Download Scientific Diagram

Handbook Fortigate Fortios 6 0 0 Fortinet Documentation Library
Internet Security Association And Key Management Protocol Isakmp
Internet Security Association And Key Management Protocol Isakmp
How To Analyze Ipsec Failures Huawei Firewall How To Analyze Ipsec Failures Huawei

Isakmp Ike Phase 1 Status Messages Mm Wait Msg Tunnelsup
Internet Security Association And Key Management Protocol Isakmp Overview Ipv6 And Ip Security

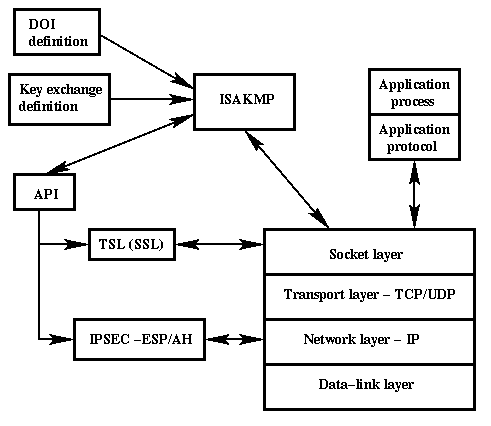
1 Placement Of Isakmp In The Network Architecture Standard Ipsec Download Scientific Diagram